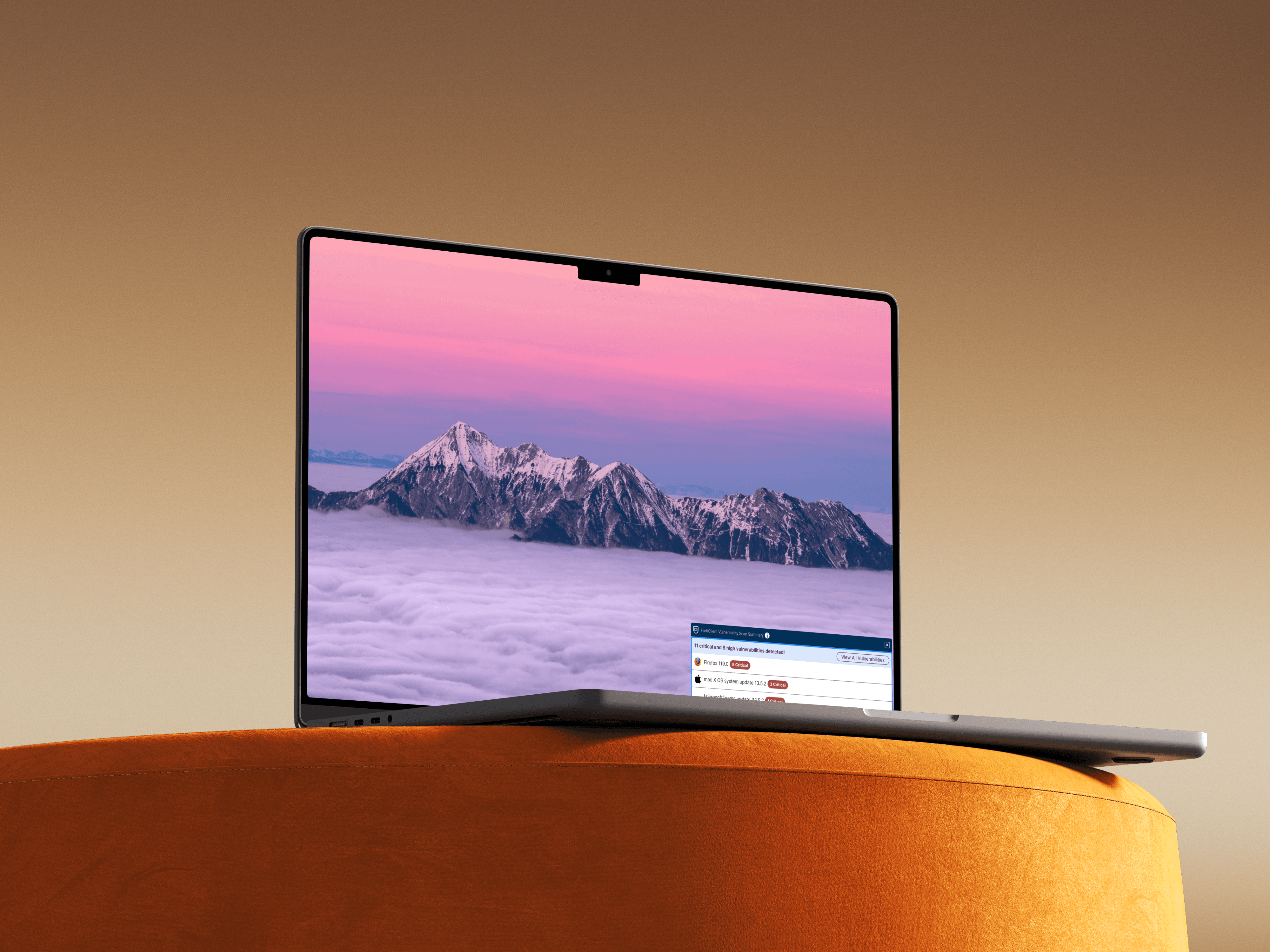
Vulnerability Alerts
Improved workflow efficiency by 92%, saved $600k in internal operational cost
FortiClient is an endpoint security agent that continuously monitors activity across deployed devices including laptops, desktops, and mobile phones. As part of this protection, FortiClient regularly scans endpoints for vulnerabilities: software dependencies that can be remotely exploited by malicious actors. On average, a single endpoint is exposed to more than 40 new vulnerabilities every week.
Research revealed that Fortinet IT administrators manage over 10,000 endpoints, all of which were never proactively notified when vulnerabilities were detected. The core challenge was scale. Administrators relied on manual outreach to inform users of required remediation, a process that was time-consuming, inconsistent, and difficult to sustain.
As UX Lead, I designed an end-to-end solution grounded in workflow redesign and journey mapping. The resulting experience delivered 99% visibility into endpoint vulnerabilities across the organization and improved IT remediation workflows by over 90%, significantly reducing manual effort and operational overhead.
The solution was recognized and praised by Fortinet’s Executive Vice President of Product Management, Robert May, for its usability, vision, and scalability.
Product
Web design
Skills
User research & testing
Painpoint discovery
Stakeholder management
Product design
Interactive prototyping
Public speaking
Role
Lead designer
Team
Kunal Marwah, Thiago Santana, Tony Huang, Kelvin Tao
Timeline
March - August 2024
Overview
As Lead UX Designer for the Vulnerability Alert Project, I drove the initiative from concept through implementation, partnering closely with product management and engineering.
Historically, FortiClient did not proactively alert users when vulnerabilities were detected. After a manual or automated scan, vulnerabilities were silently displayed within the interface. If users were not actively viewing the page at that moment, the detections went unnoticed.
The business goal was straightforward: design a customizable alerting system that informs users of critical vulnerability detections on their endpoints, as defined by IT administrators.
While IT administrators could view vulnerability events, there was no clear path from detection to remediation. Vulnerability data existed, but it was disconnected from action. As a result, the system functioned as a passive reporting tool rather than an effective response mechanism. I redefined the approach by designing a workflow that bridged this gap enabling administrators to move seamlessly from identifying vulnerabilities to driving remediation, significantly streamlining the process.
Although the goal was clear, alignment on the solution was not. Engineering leadership favored the path of least resistance by reusing existing interfaces without workflow changes. Product management sought a simple implementation, while UX focused on long-term usability and scalability. Without a cohesive, scalable design, the effort risked becoming a superficial interface update rather than a true vulnerability alert system.
I led the design of a solution that:
Enabled administrators to define which vulnerabilities trigger user alerts
Automatically notified users whenever a qualifying vulnerability was detected on their endpoint
Created a clear, actionable path from detection to remediation
This approach transformed vulnerability alerts from passive visibility into an active, scalable security response system.
Business Goal
This feature was requested by the CTO due to the critical risk posed by unchecked vulnerabilities on endpoints. Product management initially positioned the capability as a potential upsell for the premium FortiClient license.
Research
To validate both the product and user need, I conducted in-depth user research focused on understanding existing behaviors, pain points, and expectations. The research explored:
How IT administrators currently identify, communicate, and notify users about endpoint vulnerabilities
The key pain points and inefficiencies within existing remediation workflows
What an ideal vulnerability alert and remediation solution would look like from both the administrator and end-user perspectives
The insights gathered directly informed the feature scope, workflow design, and prioritization—ensuring the solution addressed real operational challenges rather than assumed needs.
To further synthesize the findings, I created a journey map of the existing workflow. This exercise surfaced critical usability gaps, friction points, and opportunities for improvement, providing a clear foundation for the redesigned experience.
Discovery
User interviews revealed that administrators spend approximately 10 minutes notifying a single user about certain high-severity vulnerabilities via email or Microsoft Teams.
At an enterprise scale of approximately 10,000 employees, if just half of users are affected, a single large-scale manual notification campaign would require roughly 833 hours of administrative effort. At an average fully loaded cost of $75 per hour, this represents more than $62,000 in labor cost per campaign.
For organizations experiencing even one such event per month, the annual cost exceeds $700,000 highlighting a significant scalability and cost-efficiency challenge in the current workflow. This is not only for Fortinet but also for similarly sized enterprise clients. This highlights a clear scalability and cost-efficiency problem.
The journey map also revealed some core pain points and opportunities which are highlighted below.
Design Synergy
This was one of the most challenging projects I led at Fortinet, not because of the design complexity, but due to the resistance I encountered along the way.
When I presented these findings, the reaction from stakeholders was mixed. Many believed that simply consolidating all events into a single view would be enough to improve the experience for premium license holders. To challenge this assumption and gain buy-in, I had to be patient, present compelling evidence, and reframe the problem in terms of lost time, inefficiency, and the potential business risks posed by delays in remediation.
After I gained buy-in from key stakeholders, we aimed to hit two critical goals with a single, efficient solution that would address both the business and user needs.
Executive Validation
Our solution was a web interface that not only consolidated endpoint events into one unified view but also provided detailed file path information for vulnerability events. This streamlined the admin’s workflow, improving efficiency while addressing key pain points.
This wasn’t just a design deliverable it became a shared vision. The prototype acted as a bridge between design, engineering, and product, allowing the entire team to interact with the concept, and understand the full remediation flow before a single line of code was written.
Through multiple feedback rounds with real admins, we validated key usability improvements and ensured the solution addressed every core pain point identified during research. What started as a controversial project evolved into a collaborative success, uniting cross-functional teams around a clear, user-centered vision.
Solution
The final design delivered a suite of enhancements that completely transformed how IT administrators viewed and resolved threats.
Admins could now see the full file path directly from the event table, eliminating the need for cumbersome requests for screenshots or relying on end users for critical details. Each event entry was now linked seamlessly to guided remediation workflows, allowing admins to investigate, validate, and act all within EMS.
This closed the gap between event visibility and actionable remediation, turning what was once a passive monitoring experience into a robust, end-to-end remediation workflow.
Reporting: Built-in reporting tools for generating actionable insights and compliance documentation.
Multi-Event Action: Admins could address multiple events at once, reducing time spent on manual triage and response.
Limitations
While the solution significantly improved the user experience, there are still areas for potential enhancement:
Scalability: While the solution works well for smaller teams, larger environments may require further optimization for handling massive amounts of endpoint data.
Advanced Customization: Additional customization options for more complex workflows could help improve flexibility for power users.
Integration with Other Systems: The feature could be further enhanced by integrating with third-party tools or extending compatibility with more IT systems.
Phase 2
The final design delivered a suite of enhancements that completely transformed how IT administrators viewed and resolved threats.
Admins could now see the full file path directly from the event table, eliminating the need for cumbersome requests for screenshots or relying on end users for critical details. Each event entry was now linked seamlessly to guided remediation workflows, allowing admins to investigate, validate, and act all within EMS.
This closed the gap between event visibility and actionable remediation, turning what was once a passive monitoring experience into a robust, end-to-end remediation workflow.
Limitations
While the solution significantly improved the user experience, there are still areas for potential enhancement:
Scalability: While the solution works well for smaller teams, larger environments may require further optimization for handling massive amounts of endpoint data.
Advanced Customization: Additional customization options for more complex workflows could help improve flexibility for power users.
Integration with Other Systems: The feature could be further enhanced by integrating with third-party tools or extending compatibility with more IT systems.
Validated Impact
By bridging the gap between data and action, the feature enabled IT teams to resolve incidents faster and with greater confidence. What was once a multi-day, fragmented process became a seamless, end-to-end experience cutting remediation time by 23+ hours per case and saving Fortinet IT organizations over $100K annually in productivity and support costs.
Hours saved per remediation
0Hours
Remediation Package Creation Improvement
0%
Admin Hours Saved in USD/yr
$0